Their most
modern and (in theory) secure system was the M-138-A
strip cipher. Unfortunately for the Americans this system was compromised
and diplomatic messages were read by the Germans, Finns, Japanese, Italians and
Hungarians. The strip cipher carried the most important
diplomatic traffic of the United States (at least until late 1944) and by
reading these messages the Axis powers gained insights into global US policy.
The strip
cipher was not a weak system cryptologically, even though it could not offer
the security of cipher machines. The success of German and Finnish codebreakers
was facilitated in many cases by the poor way that the system was used by the
State Department.
Use of the
M-138 strip cipher by the State department
Each embassy
had 50 ‘circular’ alphabet strips and 50 ‘specials’. The ‘circulars’ were used
for communications between embassies and for messages from Washington to all
embassies. The ‘specials’ were used for direct communications between
Washington and a specific embassy.
The way the
system worked was that each day 30 alphabet strips were chosen out of the
available 50 (both for the ‘circulars’ and the ‘specials’). The strips used and
the order that they were inserted in the metal frame was the ‘daily key’.
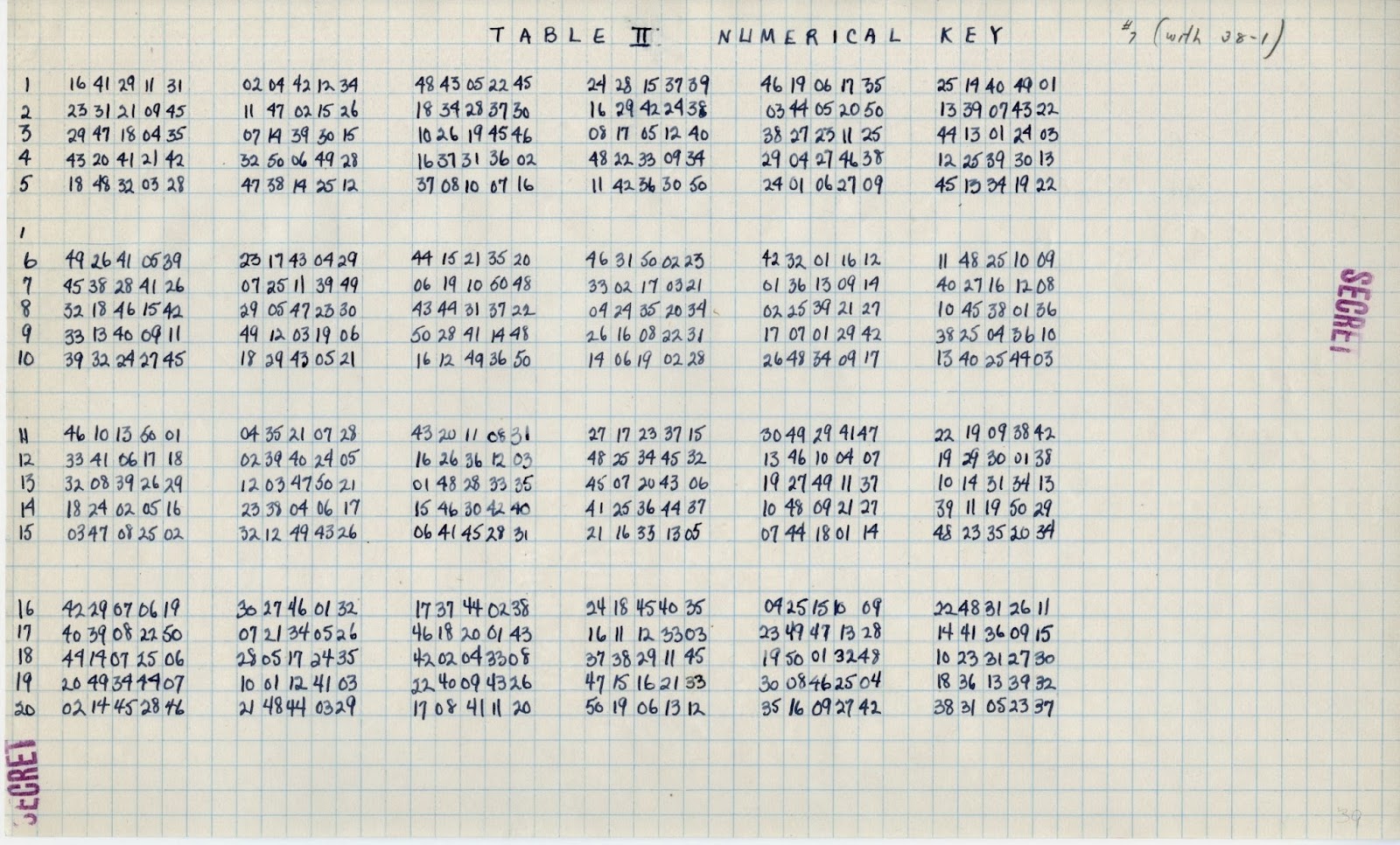
The strip system did not have a separate ‘key’ for each day. Instead there were only 40 different rearrangements for the entire year.
The daily key
table indicated which of the 40 keys was valid for the specific day. For
example in the following table assuming that the date is April 10 then the
numerical key to be used is 30.The strip system did not have a separate ‘key’ for each day. Instead there were only 40 different rearrangements for the entire year.
Using the 30th numerical key we would insert in the panel first the alphabet strip with the number 19, then in the second position no43, in the third position no24……… and finally in the 30th position no21.
Obviously having only 40 keys was not the best choice. Enemy codebreakers would only need to solve the traffic of 2 months and then they would have recovered almost all the numerical keys. Although I’ve accused the State Department for misusing the M-138-A in this case they were simply following the same instructions as the US Armed Forces.
According to Special Research History SRH-366 ‘History of Army Strip Cipher devices’ the US Army also used a daily key table (but with 50 keys) till mid 1942. From then on they introduced a separate key for each day and the list was changed each month.
This change however was not implemented by the State Department. Was
this the only mistake of the State
Department’s cipher unit? Apparently not.
Reuse of
alphabet strips and key lists
According to the
information presented so far it is clear that the strip system was based on the
daily key table, the numerical key and the alphabet strips. Enemy codebreakers
would need to recover all three parts in order to solve large numbers of
messages. The only other way was to attack messages individually and that was
too costly in terms of time and manpower.
The work of German
and Finnish codebreakers was made much easier due to the fact that all three
parts of the strip system were reused. Let’s have a look at the available
information from postwar reports.
From TICOM I-201
‘Interrogation of Franz Weisser , Dr Phil Studienassessor of Anglo-American
section of OKW/Chi’, p3
The small Finnish staff under Colonel
HALLAMAA also collaborated quite effectively giving hints. Thus it found out
that the systems used in different
countries after some time emerged again in other countries.
From TICOM
I-145 ‘Report on the US strip system by Reg Rat Dr Huettenhain’
Only a
little of the material received could be read at once. Generally it was back traffic that was read.
As, however, the different sets of
strips were used at different times by other stations, it was possible, in isolated cases, to read
one or the other of the special traffics currently.
The use of the same alphabet strips by
different embassies is confirmed by a Japanese message listing the different
strips and the posts that used them. This was information they received from
the Finnish
codebreakers.
According to
a US report from November 1943 the same strips were used by 2-4 stations but an
effort was underway to introduce new ones, used by only 2 holders at the same
time:
‘The old systems did not use channel elimination and the same set of strips was sometimes held by 2 to 4 stations, however new systems using channel elimination and limited to 2 holders are being distributed as fast as possible’
Thanks to the continued use of alphabet strips the Axis codebreakers only needed to recover the daily key tables and numerical keys.
Or did they?‘The old systems did not use channel elimination and the same set of strips was sometimes held by 2 to 4 stations, however new systems using channel elimination and limited to 2 holders are being distributed as fast as possible’
Thanks to the continued use of alphabet strips the Axis codebreakers only needed to recover the daily key tables and numerical keys.
According to
David Kahn in 'Finland's Codebreaking in World War II':
‘Each post
had its own set of strips; the key changed daily but was the same for all
posts. This cryptographic weakness was probably permitted for logistical
reasons.’
If the daily
key for the ‘special’ strips was the same for all posts that would mean they
had the same daily key table and numerical key.
Originally I thought that this could not have been allowed by the State Department and instead it was a reference to a limited number of daily key tables and numerical keys for use with the ‘special’ strips but according to a series of security studies submitted to the US Joint Chiefs of Staff in 1944 it is exactly what was happening during the war.
Investigations were carried out in June 1941, November and December 1943 and June 1944.
These
investigations identified numerous problems with State Department security such
as poor procedures for securing classified material, unclear classification
procedures, use of compromised codebooks, operator mistakes, inadequate
training program for cipher personnel etc etc.
In the field of cryptology the main problems were the limited number of cipher machines in use, the continued use of codebooks that were considered to be compromised and in the case of the M-138-A strip cipher the use of the same keylist by several holders of the system. This problem was identified not only in the 1944 survey but also in the 1943 one.
ConclusionOriginally I thought that this could not have been allowed by the State Department and instead it was a reference to a limited number of daily key tables and numerical keys for use with the ‘special’ strips but according to a series of security studies submitted to the US Joint Chiefs of Staff in 1944 it is exactly what was happening during the war.
Investigations were carried out in June 1941, November and December 1943 and June 1944.
In the field of cryptology the main problems were the limited number of cipher machines in use, the continued use of codebooks that were considered to be compromised and in the case of the M-138-A strip cipher the use of the same keylist by several holders of the system. This problem was identified not only in the 1944 survey but also in the 1943 one.
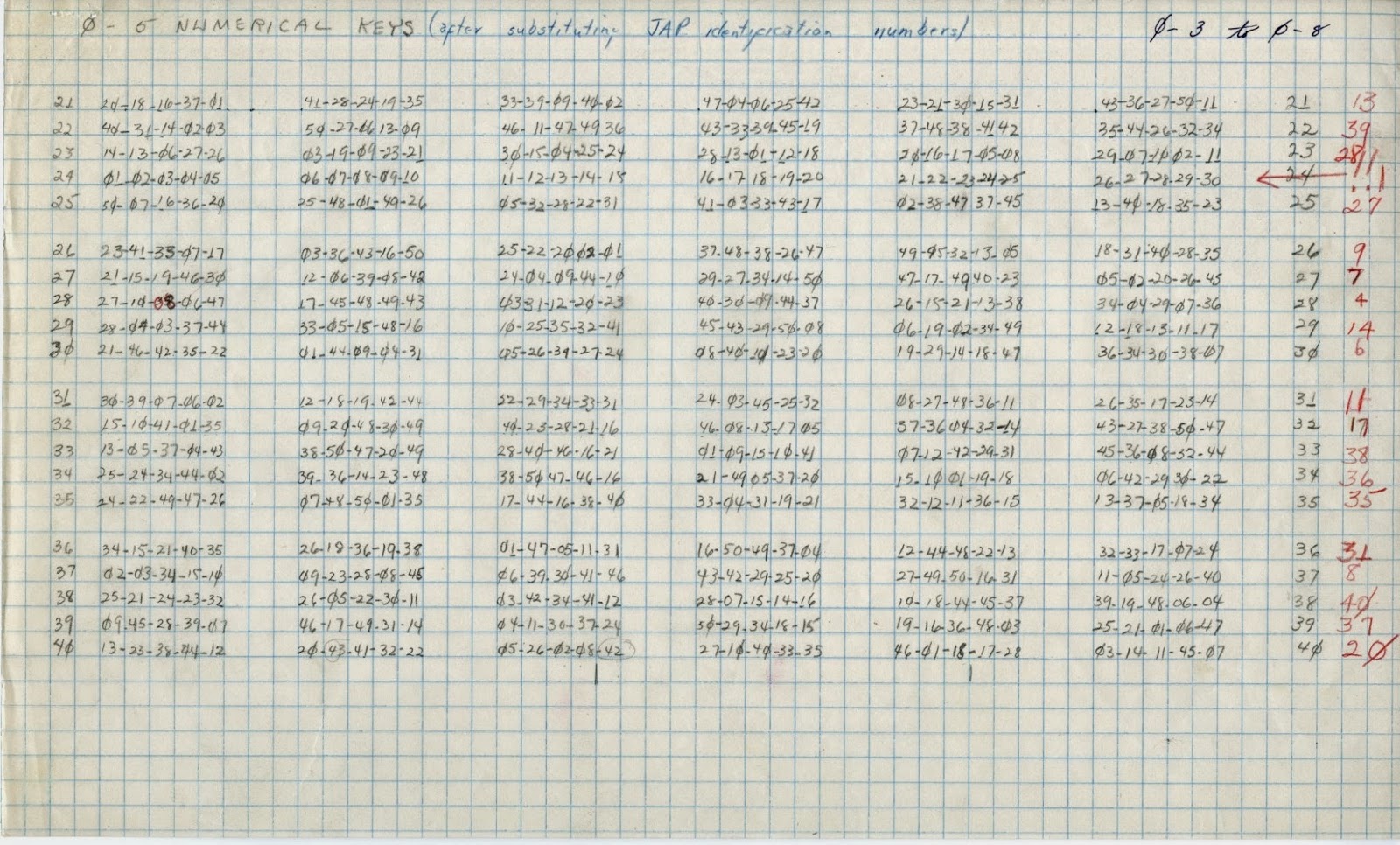
For example the following
key list and numerical keys were used with the ‘circular’ strips 0-3 (introduced
in March 1943) to 0-8 (introduced in August 1943).
From the JCS security surveys it is obvious that the State Department’s communications security had many weak spots both in handling classified material as well as transmitting them securely. The main problem was the limited number of secure cipher machines and the continued use of systems that were either considered to be compromised or were vulnerable to operator errors.
The M-138-A
strip cipher was cumbersome to use but offered adequate security provided it
was used properly. Unfortunately the State Department’s cipher unit has to take
the blame for using this system in an awkward manner and thus making the work
of the Axis codebreakers much easier than it should have been.
The major problems in the period 1940-43 were the use of
only 40 ‘keys’ for the period of validity, the use of the same 'special' strips
by several embassies and the coupling of the ‘special’ strips with only
one keylist. Also the fact that consecutive editions of both ‘special’ and ‘circular’
strips used the same keylists.
The State Department implemented security changes in 1943
and early 1944 and these limited the Axis success but did not defeat it.
Specifically:
1). From March 1943 a new set of circular strips was used
for each month (0-4 for April, 0-8 for August etc, the strips used in 1944 were
numbered 0-13 to 0-24).
2). By 1944 most embassies were using a different ‘special’
alphabet set for each month (for example strips 69-1 to 69-12 were used by the
embassy in Spain).
3). The embassy in Bern, Switzerland received 6 new cipher
systems in June 1943. In July they started using the strips 60-3 for
intercommunication between Bern, London, Lisbon, Algiers and Washington.
4). A set of strips titled 00-1 (and key table C) was
introduced in late 1943 for enciphering the confidential traffic of other US
government agencies such as the Office of Strategic Services, Office of War
Information and Military Intelligence Service, Foreign Economic
Administration, War Shipping Administration, Office of Lend-Lease
Administration and the War Refugee Board.
5). Channel elimination was introduced for most stations in
January 1944.
According to German and Finnish accounts these measures hindered
their efforts but even in 1944 they could still read some M-138-A traffic,
since some embassies continued to use old alphabet strips that had been solved
in previous years.
Sources:
SRH-366 ‘The history of Army strip cipher devices’, NARA - RG 457 - Entry 9032 Box 214 – ‘M-138-A numerical keys/daily key table/alphabet strips’, Friedman collection (NSA website), TICOM reports I-2, I-84, I-145, I-201, British National Archives HW 40/132 ‘Decrypts relating to enemy exploitation of US State Department cyphers, with related correspondence’, NARA - RG 457- Entry 9032- box 1384- NR 4400 'JCS Ad hoc committee report on cryptographic security of government communications', NARA - RG 59 - M-973 ‘Purport Lists for the Department of State Decimal File 1910-1944’ – rolls 444, 611 (119.25 strip cipher).
Sources:
SRH-366 ‘The history of Army strip cipher devices’, NARA - RG 457 - Entry 9032 Box 214 – ‘M-138-A numerical keys/daily key table/alphabet strips’, Friedman collection (NSA website), TICOM reports I-2, I-84, I-145, I-201, British National Archives HW 40/132 ‘Decrypts relating to enemy exploitation of US State Department cyphers, with related correspondence’, NARA - RG 457- Entry 9032- box 1384- NR 4400 'JCS Ad hoc committee report on cryptographic security of government communications', NARA - RG 59 - M-973 ‘Purport Lists for the Department of State Decimal File 1910-1944’ – rolls 444, 611 (119.25 strip cipher).
















No comments:
Post a Comment