The NSA and GCHQ use the internet To 'Manipulate,
Deceive And Destroy Reputations'
Military and intelligence history mostly dealing with World War II.
Tuesday, February 25, 2014
In the news
Should
the NSA be broken into separate parts?
Saturday, February 22, 2014
James Bamford NSA video
Interesting
presentation on the history of the NSA by author James Bamford
Wednesday, February 19, 2014
Saturday, February 15, 2014
RAF Strength Far East Command – January 1942
In December
1941 Japan entered WWII on the side of the Axis by attacking the forces of the
USA and UK stationed in the Pacific.
These forces were not capable of standing up to the modern Japanese planes, especially the Mitsubishi A6M Zero.
The most
audacious attack was against the US fleet in Pearl
Harbor but in the same period the Japanese invaded the Philippines,
Thailand
and British controlled Hong
Kong and Malaya.
Both the
Americans and the British had underestimated Japan’s military and they paid the
price. The British also suffered from their ongoing war against Germany and
Italy. They had limited military resources and the choice had been made to
concentrate these in Europe. Thus their forces in the Far East were equipped
with outdated weapons. This is obvious in the case of the RAF, as shown by the
following strength reports:
Source: AIR
22 ‘Air Ministry: Periodical Returns, Intelligence Summaries and Bulletins’
The types available
were second line aircraft like the Hawker
Audax, Westland Wapiti, Westland Lysander, Vickers Vildebeest and a
handful of relatively modern Curtiss
P-36, Bristol Blenheim, Bristol Beaufort, Lockheed Hudson and Brewster F2A Buffalo. These forces were not capable of standing up to the modern Japanese planes, especially the Mitsubishi A6M Zero.
Sunday, February 9, 2014
British cryptologic security failures in WWII
Signals
intelligence and codebreaking played an important role in WWII. British and
American codebreakers solved many important Axis crypto systems, such as the
German Enigma machine and the Japanese Navy’s code JN25.
Historians
have not only acknowledged these Allied successes but they’ve probably
exaggerated their importance in the actual campaigns of the war.
Unfortunately
the work of the Axis codebreakers hasn’t received similar attention. As I’ve
mentioned in my piece Acknowledging
failures of crypto security all the participants suffered setbacks from
weak/compromised codes and they all had some successes with enemy systems.
Britain, the
Soviet Union and the United States did not have impenetrable codes. In the
course of WWII all three suffered setbacks from their compromised
communications.
Time to take
a look at the British side and their worst failures.
Book
cyphers
The basic
British cryptosystem for important radio-traffic was the enciphered codebook. These
4-figure codebooks were enciphered with subtractor tables, using the
non-carrying system. The military services had their own series of cyphers such
as the War
Office Cypher for the Army and the RAF cypher
for the airforce plus there were diplomatic editions for the Foreign Office and
the Interdepartmental
Cypher that was used both by the services and the civilian organizations.
The codebook
was basically a dictionary that
assigned a 4-figure group to each word. For example the word ‘division’ would
have the code 5538, ‘attack’ 2090, ‘artillery’ 0231 etc etc
So the cipher clerk would first use the codebook in order to find the
code groups corresponding to the words of the message and then he would have to
use the subtractor tables in order to encipher them. This means that each
codegroup would be subtracted from the key groups (of the subtractor table) without
carrying over the numbers.Thursday, February 6, 2014
Sunday, February 2, 2014
State Department’s strip cipher – reuse of alphabet strips and key lists
During WWII
the US State Department used several cryptosystems in order to protect its
radio communications from the Axis powers. For low level messages the unenciphered
Gray and Brown codebooks were used. For
important messages four different codebooks (A1,B1,C1,D1) enciphered with
substitution tables were available.
Their most
modern and (in theory) secure system was the M-138-A
strip cipher. Unfortunately for the Americans this system was compromised
and diplomatic messages were read by the Germans, Finns, Japanese, Italians and
Hungarians. The strip cipher carried the most important
diplomatic traffic of the United States (at least until late 1944) and by
reading these messages the Axis powers gained insights into global US policy.
The strip
cipher was not a weak system cryptologically, even though it could not offer
the security of cipher machines. The success of German and Finnish codebreakers
was facilitated in many cases by the poor way that the system was used by the
State Department.
Use of the
M-138 strip cipher by the State department
Each embassy
had 50 ‘circular’ alphabet strips and 50 ‘specials’. The ‘circulars’ were used
for communications between embassies and for messages from Washington to all
embassies. The ‘specials’ were used for direct communications between
Washington and a specific embassy.
The way the
system worked was that each day 30 alphabet strips were chosen out of the
available 50 (both for the ‘circulars’ and the ‘specials’). The strips used and
the order that they were inserted in the metal frame was the ‘daily key’.
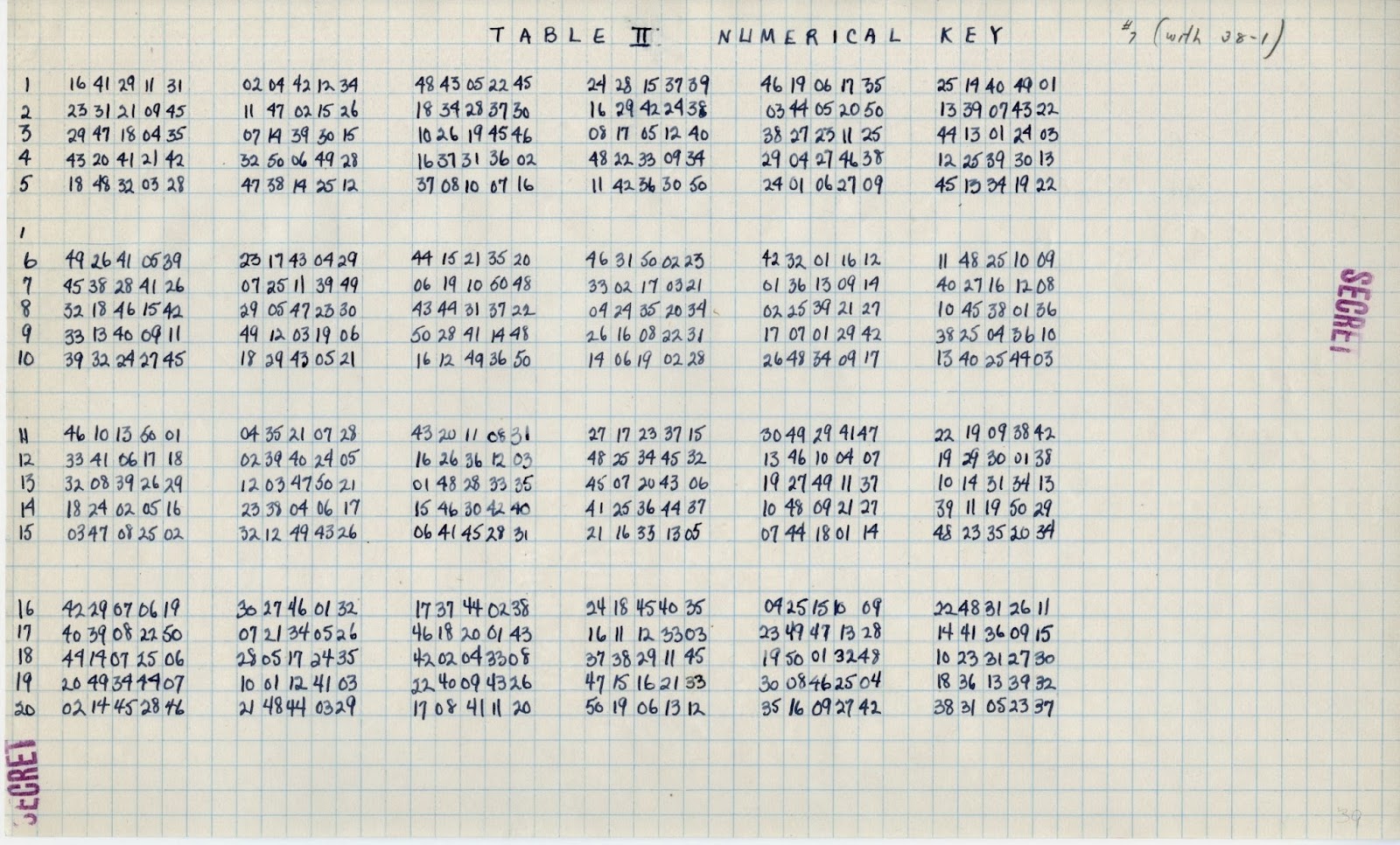
The strip system did not have a separate ‘key’ for each day. Instead there were only 40 different rearrangements for the entire year.
The daily key
table indicated which of the 40 keys was valid for the specific day. For
example in the following table assuming that the date is April 10 then the
numerical key to be used is 30.The strip system did not have a separate ‘key’ for each day. Instead there were only 40 different rearrangements for the entire year.
Subscribe to:
Comments (Atom)